News
Huawei shared 5G transmission network clock security assurance plan

The latest information revealed that Huawei, Beijing Mobile, and the Network Division of China Mobile jointly published the 5G transmission network clock security assurance plan.
As the name suggests, the above-mentioned firms designed this approach, which strives to identify the transmission network using 5G technology and ensures the 1588v2 clock’s strong and steady operation.
At present, time synchronization is an obligation for a stable connection between inter-station coordination features of 5G technology.
In any case, if an irregular synchronization occurs it creates interruption among base stations. As a result, users encounter problems such as call slips.
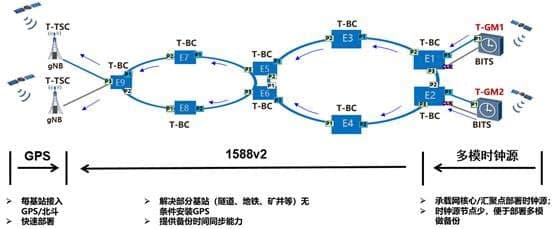
As a solution to this problem, Huawei and China Mobile introduced the satellite clock + transmission network 1588v2 clock for constant synchronization. To date, the 1588v2 has been completely deployed but still has room for further improvement.
However, the reliability of the 1588v2 clock is facing two major challenges regards the network topology. We can describe them in the following words-
- At present, the 1588v2 deployment is done manually, which leads to problems such as misconfiguration, tracking problems, etc.
- The irregular occurrence like optical cable cutover, topology transformation, clock topology changed for the passive node causes unusual time synchronization.
Concerning the above issues, it’s important to supervise the network configuration and network modules for 15888v2.
Previous Works:
Huawei, China Mobile, and Beijing Mobile jointly conducted the “5G Transmission Network Clock Security Program” back in March this year. The main motive of this program is to search and analyze the 1588v2 transmission clock configuration verification and automatic deviation risk analysis techniques.
After a period of continuous research, the firms drive a solution based on digital intelligence algorithms and 5G technology to solve the problem. It works on a restrictive platform to connect SPN transmission, BITS, and wireless networks.
Furthermore, and uses intelligent algorithms to deal with 1588v2 configuration, risk links, lower quality, output problems, provincial two-level monitor perspectives, analyze problems, and so on.
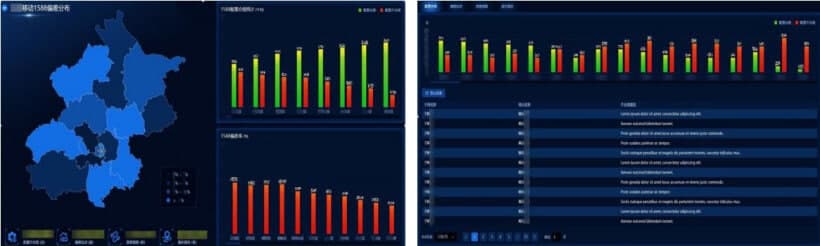
Results:
After the implementation of this solution, the manual verification resource for the 1588v2 configuration has been reduced to 0.25 persons in a day. Previously it took 12 persons to do this for a day.
Moreover, the efficiency has been increased by 50 times, simultaneously the problem of the time-consuming problem has also been much better.
(Via- C114)







