Bugs and Issues
Huawei Nova 5T users facing WiFi connectivity and battery drain issue after upgrading over EMUI 11

The quad rear camera phone – Huawei Nova 5T, is powered by Kirin 980 flagship processor and comes with the latest design that interacts with the user.
Talking about its operating, it was initially packed with Android-based OS EMUI 9.1 and further receiving EMUI 10, EMUI 10.1, and EMUI 11 major software upgrades that provide a new user experience.
The EMUI 11 rollout for Nova 5T is soon going to conclude worldwide. To date, most of the devices were upgraded over EMUI 11 in different parts of the globe. The latest custom OS brings a number of new features that enhance system performance and provide a new user interface.
After installing EMUI 11, some Huawei phone users and Bjørnar Svanes from Norway reported some bugs and issues with their respective models. One thing worth mentioning, not every user is satisfied with new offerings or these updates may create some problem in existing systems.

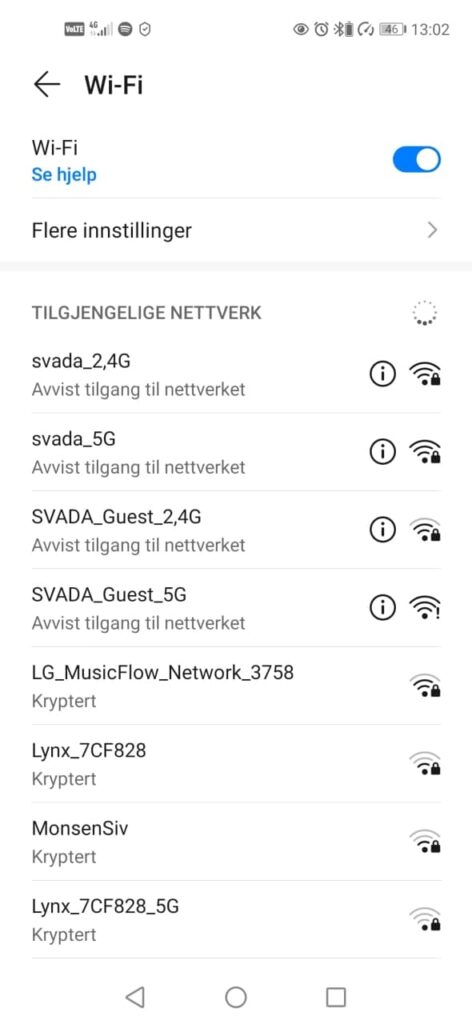
Recently, a Huawei Nova 5T user contacted us and informed us about a WiFi network and battery drainage issue pop up on his smartphone after shifting on EMUI 11 from EMUI 10.1.
According to the user, after EMUI 11 update, he is facing problems in connecting local home WiFi and observed that the battery is draining very fast compared to the EMUI 10.1. He added that previously the WiFi gets connected normally but now many times a day “Rejected access to network” notification pop-ups.
This issue reporter believes that 99.5% it’s all happing because of the latest major update and requesting Huawei to deliver a new network stability update to resolve this problem. Also, he is regretting why he updated to the new EMUI version when he is happy with the existing version.
However, here’s a quick solution to this problem that may help.
To solve this network problem, two option are there:
- Revert to EMUI 11 to EMUI 10.1
- Rollback to EMUI 10.1 and re-install the EMUI 11 upgrades
We recommend the user back up the data and roll it back to EMUI 10.1 via using HiSuit app on PC and Mac. If the user wants to again upgrade to EMUI 11 then try via the HiSuite with a proper installation.
Screenshot provided by the user: