News
BrutePrint can attack Android and HarmonyOS phone’s fingerprint
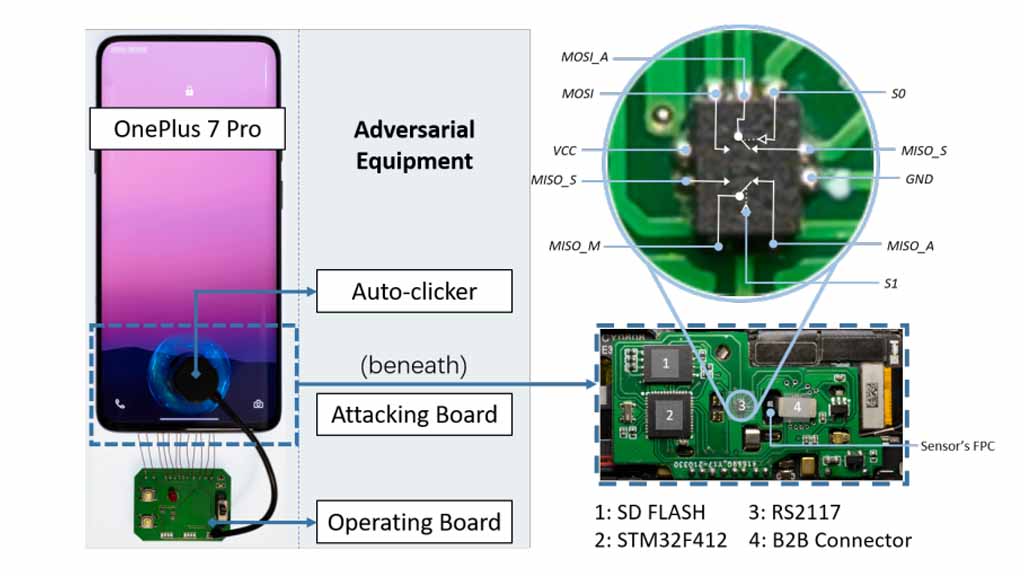
Recent research has exposed a new bluet force attack vulnerability “BrutePrint” in Android, HarmonyOS, and iOS devices, which could break through fingerprint security and get control of the device. This research is published by Xuanwu Lab, Tencent in collaboration with Zhejiang University, China.
BrutePrint attacks rely on multiple trials and errors to crack codes, keys, or passwords and gain unauthorized access to accounts, systems, or networks.
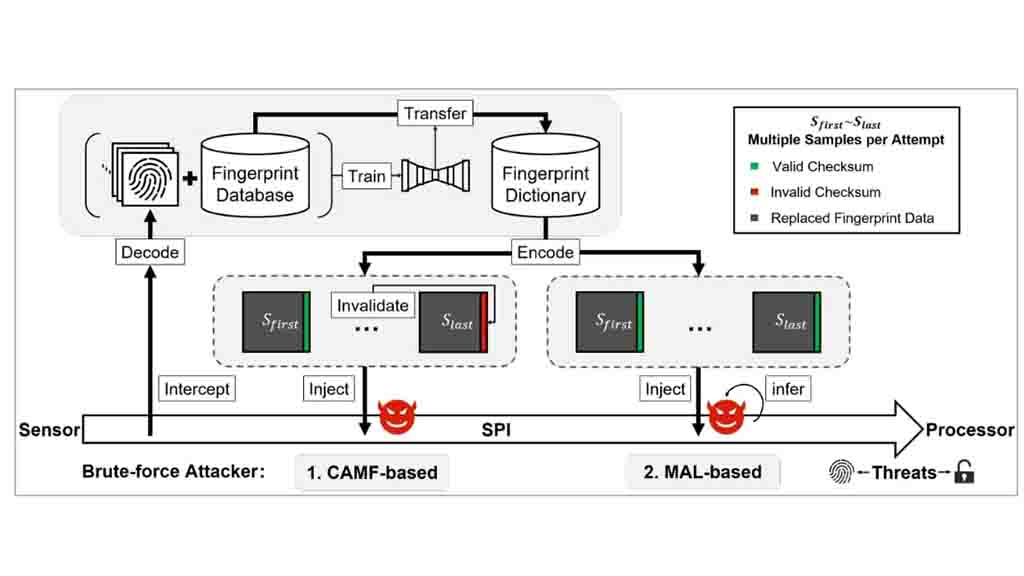
The aforementioned researchers exploited two zero-day vulnerabilities, Cancel-After-Match-Fail (CAMF) and Match-After-Lock (MAL). It is also discovered that biometric data on the serial peripheral interface (SPI) of the fingerprint sensor is not protected. Allowing a man-in-the-middle (MITM) attack to hijack the fingerprint image and thus crack the phone’s fingerprint.
In the research paper published on Arxiv.org, it is explained ten common smartphones achieved an unlimited number of attempts to crack fingerprints on all Android and Huawei HarmonyOS devices and 10 additional attempts on iOS devices.
BrutePrint:
The concept of the BrutePrint attack is to perform an infinite number of fingerprint image submissions to the target device until it matches the original fingerprint.
However, the attackers need to physical devices in order to inject the vulnerability into the target device. The research also explains that fingerprint data could be obtained from government databases or biometric data, which requires a tool at $15.

Interestingly, the researchers successfully break through the limit on the number of unlocking fingerprints through the MAL zero-day vulnerability. Thereafter, it can conduct unlimited attempts to unlock on Android and HarmonyOS phones using the “neural style transfer” system.
All fingerprint images in the database are converted based on the type of the target device sensor. As shown in the images, the fingerprint conversion capability of the device supports all capacitive, optical, ultra-thin, and ultrasonic fingerprint scanners.
10 Sample Devices:
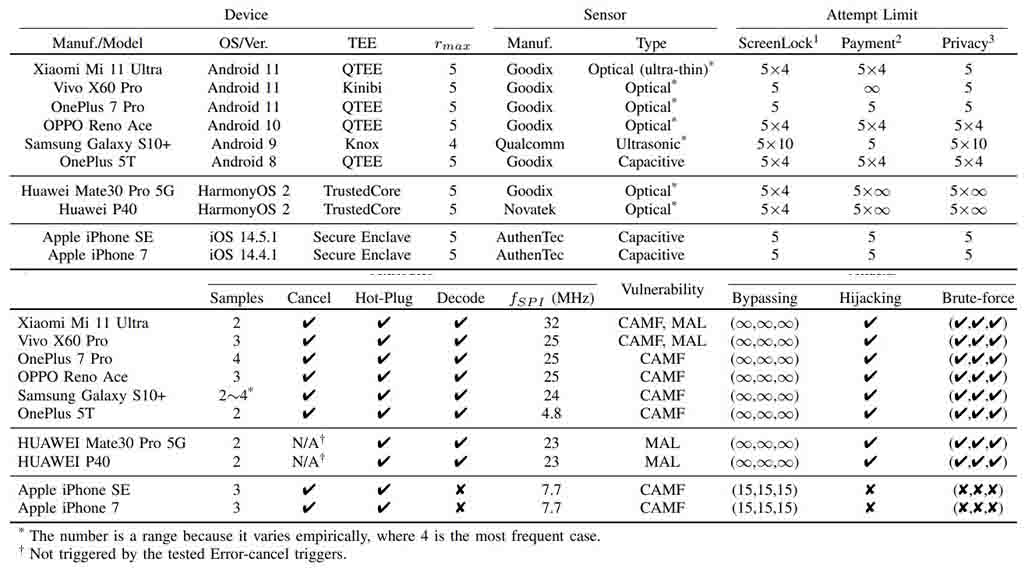
The researcher used 10 sample devices to show the BrutePrint impact. These include 6 Android, 2 HarmonyOS, and 2 Apple iPhones. The test shows that all of the devices are exposed to at least one fault. But a big fact is that Android and HarmonyOS smartphones could be attacked unlimited times.
Since iPhones already upgraded to face ID with the iPhone X series. The previous models could be affected by the attack.
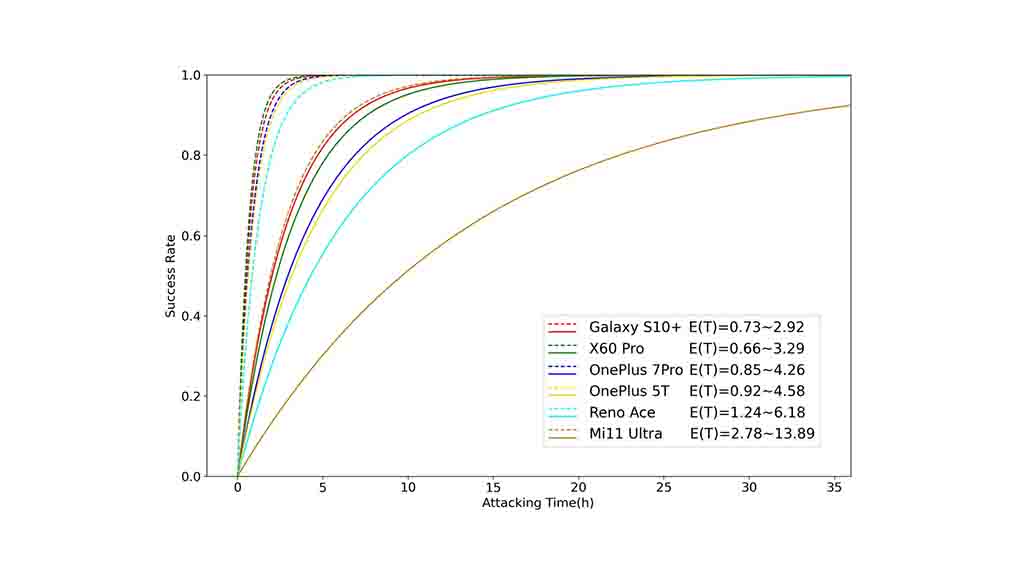
Time to crack the fingerprint:
It’s shown that the time required to break into the phone using BrutePrint ranges from 2.9 to 13.9 hours. If the phone has multiple registered fingerprints, the break-in time reduces between 0.66 to 2.78 hours.
Do I need to worry?
To recall, the BrutePrint attack requires physical access to the target device (Android or HarmonyOS, or iOS). Also, it won’t work in an instant because the attack process is lengthy in hours (as mentioned above).
So, you don’t have to worry until you give the phone to someone suspicious with the intention to hijack your data. However, this tech for bypassing fingerprint authentication is advanced and could cause serious trouble.
(via – Bleepingcomputer)






